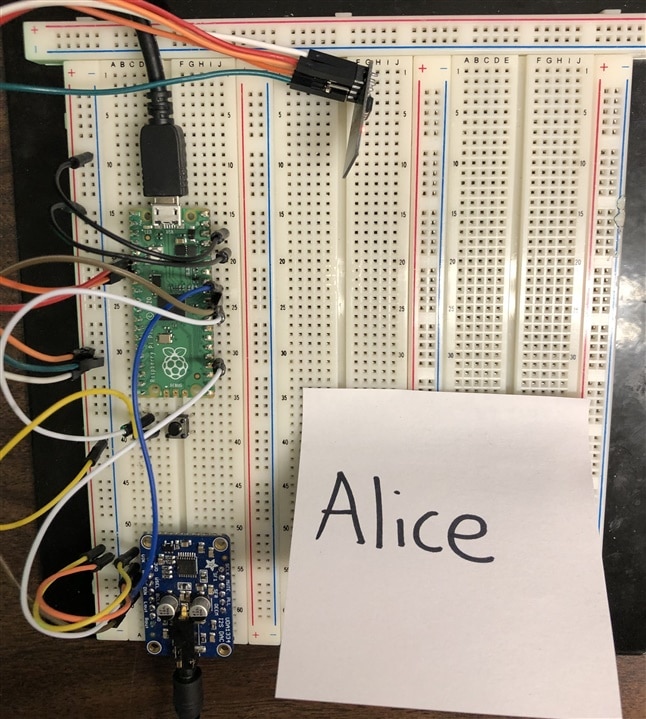
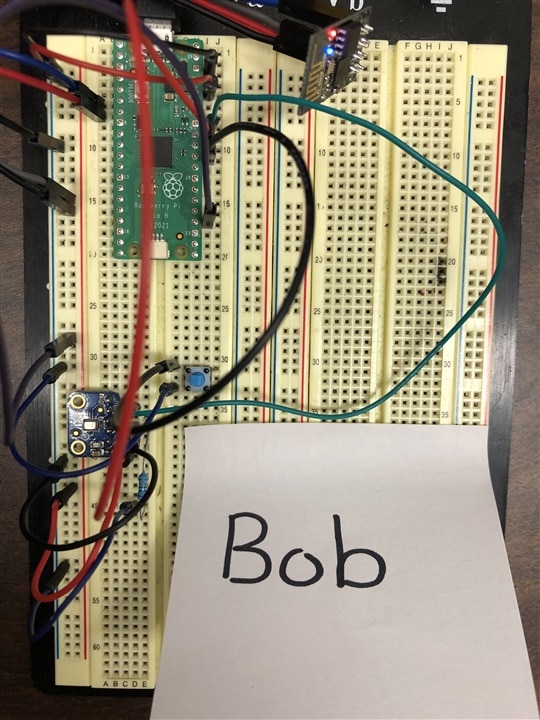
Final Goals
So far we have tested and verified that all of our individual pieces of code work. Now it’s time to integrate them and debug any problems. Let’s start with our Pico named Bob. Bob reads audio from the mic, encrypts it, sends over wifi, and even partakes in a key-exchange. This means we need to make use of our microphone code, wifi code, X3DH code, and encryption code. Similarly, Alice requires our wifi code, decryption code, and speaker code. The server requires our wifi code and a some custom code that decides what action to take depending on the message type.
Assembling Bob
We started by combining our that sends data over wifi with our code that reads the microphone. For sending audio over wifi we noticed that i2s data is 32 bits long but we cannot send all 32 bits at once since UART sends strings. Characters are 8 bits long which means the data must be split into four 8 bit characters before sending and concatenated back to 32 bits when receiving.We had tons of problems integrating the mic code so we decided to skip it and move on with combining our encryption and wifi codes. We had the expected problems such as passing by reference, the use of pointers, and using the wrong variable sizes. After resolving our issues we managed to send encrypted messages to Alice. Below are some pictures of our code working.
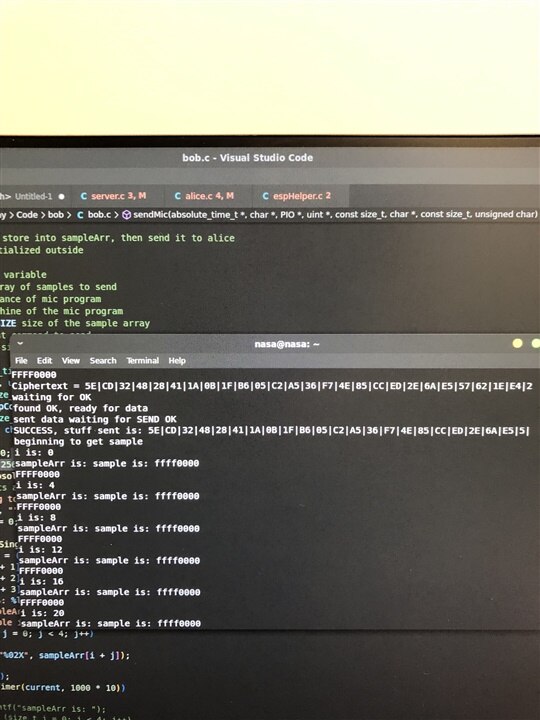
Figure: Message being encrypted and sent to Alice
Assembling Alice
With Alice, we started by combining the wifi code with the decryption code. We took the cipher text sent to us from Bob and tried to decrypt. Things went much smoother this time since we made lots of mistakes with Bob already. Since we omitted the mic code in Bob we were forced to commit the speaker code in Alice. Below are some pictures of our code working.
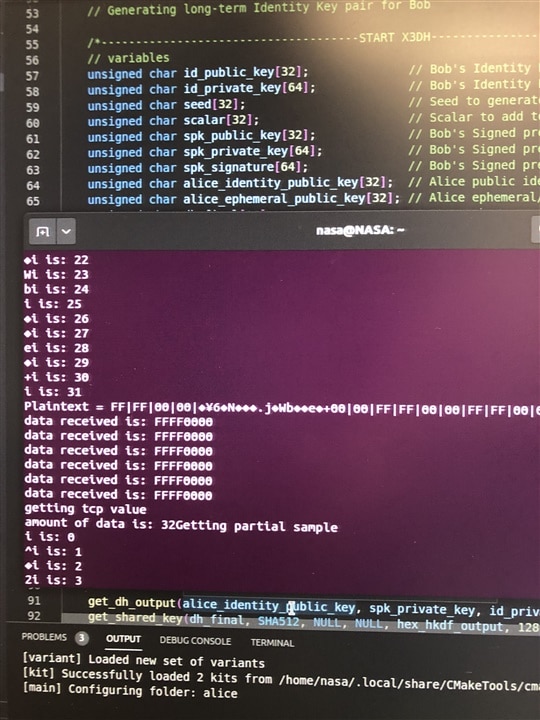
Figure: Message being received and decrypted
Final Product
Although we didn't complete everything we set out to complete, we managed to get a system working that safely sends encrypted messages over wifi using a lightweight cryptographic algorithm, perfect for small platforms. Although we 're done with this competition, our project will move forward. We have hopes of implementing this system to secure communications between the drones from another research team or to provide lightweight cryptography to biomedical devices. Below are our final pictures of Bob and Alice. Thanks to everyone who read and followed us along in our journey. It was a very fun and great learning experience for all of us.