There's a nasty vulnerability doing the rounds that's a significant concern.
https://therecord.media/libwebp-vulnerability-more-widespread-than-expected
The attack is through an infected image file, and allows an attacker to take over the browser simply by having you load the image in a page.
That obviously came as some concern to our team as we allow users to upload images to the site that then get rendered elsewhere.
I'm happy to announce that we were safe from this.
Firstly, we don't support webp files inserted into content using the insert image tool, so the only attack vector was via attachments. We also don't have any webp attachments. I checked the database and the logs and nobody has uploaded a webp.
Secondly, all our images are passed through an image optimizer before they get served to the public, as demonstrated by a screenshot of this in action in an image-heavy piece of content like BigG 's review of the Giga R1.
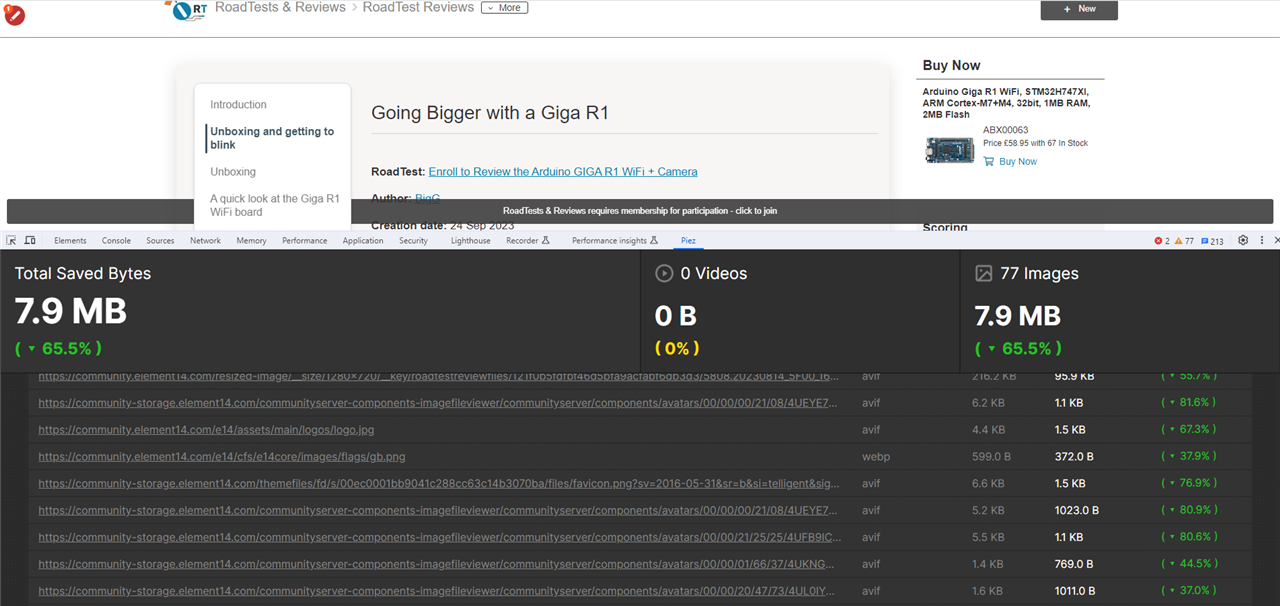
(Image manager showing it saved 7.9M of traffic on a single page by losslessly compressing the images better)
This changes the format of images to one preferred by your browser, which is sometimes webp format. But the original file was not a webp.
Image Manager is one of these really cool toys you get to play with when you administer websites that you can't remember how you ever survived without it. It saves us a ton of traffic, makes the website faster for everybody, and is almost entirely seamless
