Guaranteeing the authenticity of an edge device and the data it provides is increasingly critical as the potential for security threats grows. In the fifth blog of our remote IO blog series, we will discuss how cybersecurity is a topic of concern within the industry as connectivity and IP addressability opens up the possibility of hacking and system attacks. With edge-to-cloud connected factories generating larger volumes of data in remote locations across the factory, automation vendors must consider how to overcome several new design challenges which weren’t a problem years ago.
Why is security a problem now?
We all have heard about the connected factory of the future; well, the future is here today with all types of sensors and actuators connected together and sharing information to help the factory run as efficiently and as flexible as possible. Realizing Industry 4.0 involves increased access to edge devices in the factory and accessibility in controlling them. The resulting transparency and data insights can reduce network planning, CapEx and OpEx. Increased bandwidth and optimized machine interworking are also enabled. With that, the famous quote from the Spiderman movie comes to mind, “With great power, there must also come great responsibility.” Similarly, you cannot have all this interconnectivity that provides the power to make smarter decisions without considering the consequences.
Providing a data path from edge to cloud introduces new threat vectors, meaning that cyber security risks to Industrial Control Systems (ICS) must be reassessed. ICS cyber security solutions need to adapt to address the changing risk, and traditional countermeasures applied to the system, such as firewalls and placing a device behind a locked door, are counterintuitive to the goals of Industry 4.0. This means devices will need to be security hardened to enable increased functionality in a secure method. Identity and integrity will be at the core of every device in the field to enable trusted data and secure operation.
System designers for automation vendors, and system integrators may encounter the following issues as they are planning their system’s design (see figures 1 & 2).

Figure 1- Common Design Challenges Parts 1 - 4
Authenticity
Third-party clones or counterfeit components could enter the system and pose safety risks while not meeting the customer’s expectations and specifications, affecting system integrity and reliability.
- Certificate Management
- The ability to verify a device’s identity and update credentials as needed.
- Key Management
- If data is encrypted and decrypted, it’s important that the keys implementing this are protected so that data is secure.
- Secure Boot
- This protects against the risk of malicious firmware that could infiltrate entire systems and cause any havoc the firmware creator desires.

Figure 2 - Common Design Challenges Parts 5 – 8
IoT security
A variety of security techniques to protect against malware attacking an entire infrastructure that has not been properly secured.
- Endpoint Security
- Secures the communication between the endpoints in a system or validates that the source of the information is an authentic part of the system, see figure 3 below.
- Feature Control
- This can be a design challenge if there are different versions of a board with factory-based options or subscription-based services.
- TLS Support
- This is secure communication to and from the cloud.
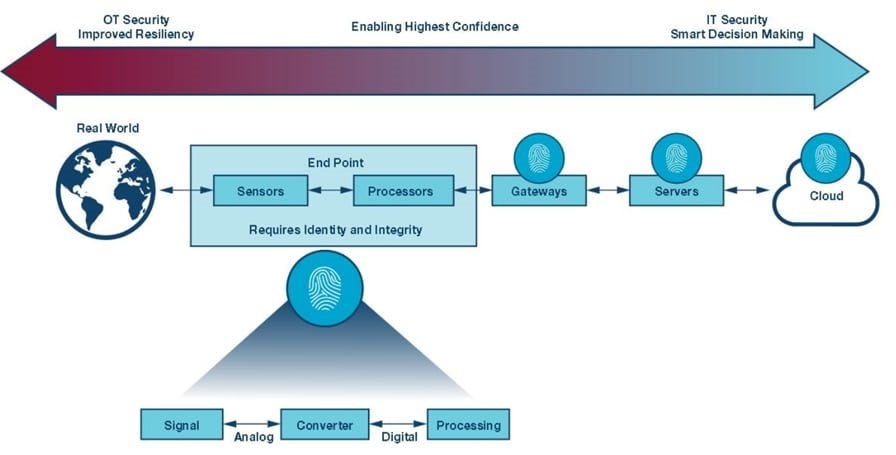
Figure 3 - Moving Security Closer to the Edge where the Data is Born
Is there a solution?
The ultra-low power MAXQ1065 Cryptographic Controller with ChipDNATM is an ideal security coprocessor for embedded devices. It can provide turnkey cryptographic functions for root-of-trust, mutual authentication, data confidentiality and integrity, secure boot, secure firmware update, and secure communications with generic key exchange and bulk encryption or complete TLS support.
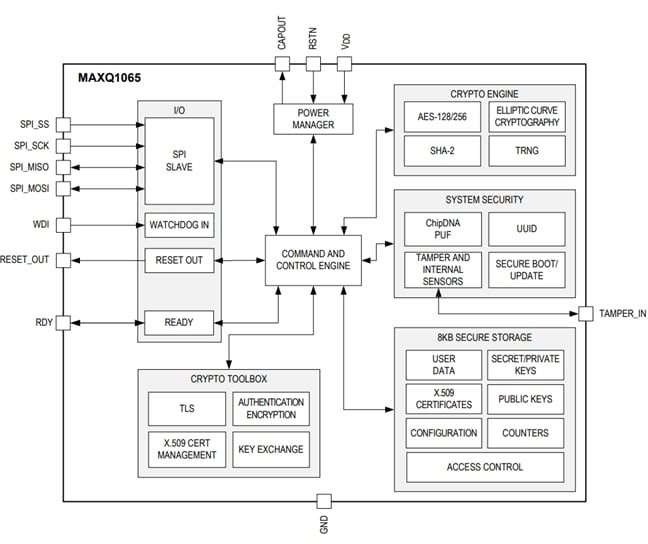
Figure 4 - MAXQ1065 Block Diagram
DeepCover® embedded security solutions cloak sensitive data under multiple layers of advanced security including active die shield, encrypted storage of keys using the ChipDNATM PUF technology, and externally callable algorithmic subroutines. Along with this, the MAXQ1065 has 8 KB of secure flash memory that can be used for keys, secrets, certificates, or user data.
The encryption (ECDSA, AES-256, SHA-256) and secure boot ROM features of the MAX32672 MCU also protect against intrusion and support the secure root of trust to ensure no malicious execution.
How does this secure the system?
The root of trust begins with safe key management. Sophisticated invasive attacks are frequently launched in an attempt to obtain cryptographic keys from secure ICs. If obtained, the security provided by the IC is thoroughly compromised. A key derived from a physically unclonable function (PUF) provides an unprecedented level of protection against invasive attacks, since the PUF-based key does not exist in memory or another static state.
Attackers can’t steal a key that isn’t there. ChipDNA provides symmetric key for encryption and decryption, as well as private keys for ECDSA and/or ECDHE. ChipDNA derives a cryptographic key from a precise analog characteristic of the IC. This key is based on a physically unclonable function and is not stored in memory or any other static state where it could be compromised. Each IC’s unique ChipDNA-generated key, since it is based on a physical unclonable function, is repeatable over temperature, voltage, and IC operating life conditions.
With legislative requirements such as the upcoming European Cyber Resilience Act (CRA), security will not only become more important, but mandated, for manufacturers of factory automation equipment/modules.
References
- Cyber Security: Securing The Edge Where Data Is Born
- DS28S60
- Secure Authenticators
- Article: Analog Devices Cyber Security Strategy To Secure The Real World
- Article: Accelerating Industry 4.0: Extending the Secure Edge in Industrial Control Systems
- Factory Automation & Process Control | Analog Devices

