The team’s robot can pull memory and read its contents. (Image credit: Ang Cui, Red Balloon Security)
We’re familiar with collecting chip data via freezing methods, but now this can be automated with robots. During the Recon reverse engineering conference, Ang Cui, Red Balloon Security founder, demonstrated a cyro-mechanical robot’s ability to extract encrypted data from DDR3 memory modules. These days, it’s difficult to reverse engineer devices because hardware manufacturers disabled JTAG debugging interfaces and UART circuitry.
Their low-cost, extremely precise robot works by freezing one RAM chip at a time rather than relying on fault injection or reverse engineering through laser ablation. They then remove the memory to read the RAM contents by placing it inside the field-programmable gate array (FPGA). In this case, they can look at the code, data, stack, heap, and all the physical memory.
Earlier this year, Cui and his team also used this technique for the Siemens vulnerability disclosure work. After removing and reading a memory chip, they had to pull off five chips since they’re interlaced. Three chips were on one side, while two were on the bottom of the board. This required the team to remove all five simultaneously, which is very complex.
Instead, they removed them one at a time, looking for the device’s deterministic execution and electromagnetic emanation. Doing so allowed them to determine where the device goes through CPU-bound operations. This approach made it possible to pull each memory chip out in tens of milliseconds. From there, they reconstructed the memory for the data, code, and bootloader. That’s sufficient time for a CNC machine to remove memory chips.
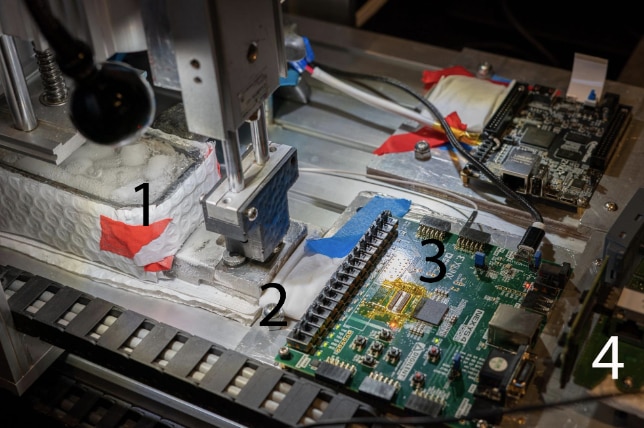
The robot, which has a CNC without the motors and X-axis actuator, attaches to a memory reader built with the FPGA and an ESP32 module-based controller running MicroPython. It simplifies the cold boot attack and features a conductive elastomer IC test socket, allowing it to perform the attack. Thanks to the socket’s flexibility, the robot can use inexpensive hardware to press the memory chips into place without causing damage.
With the FPGA-based memory reading system, a custom bootload isn’t essential to acquire code execution for dumping DRAM contents. The attack is also simplified due to the robot’s ability to move DRAM chips between the device and the readout system. The team showcased the robot on a SIMATIC S7-1500 PLC and extracted the encrypted firmware binaries. They say this approach can be used on DDR4 and DDR5 if the robot has a more costly FPGA-based memory readout system.
Have a story tip? Message me at: http://twitter.com/Cabe_Atwell

-

robogary
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Comment-

robogary
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Children