I will be working on a new project soon analyzing BLE transmitters and thought that it would be useful to have a dedicated BLE sniffer so that I could monitor the state of the Equipment Under Test (EUT).
I've used an nRF52840 Dongle on previous projects to connect my Win10 PC to BLE Dev boards and I discovered that Nordic has BLE Sniffer firmware for it, so that seemed like a good choice. The dongle is an inexpensive ($10) PCB that plugs directly into a USB-A jack.
| {gallery}nRF52840 Dongle |
|---|
|
|
|
|
Here is a link to the BLE Sniffer documentation: nRF Sniffer for Bluetooth LE
"The nRF Sniffer for Bluetooth LE software consists of firmware that is programmed onto a DK or dongle and a capture plugin for Wireshark that records and analyzes the detected data."
Since I've used Nordic tools in the past and also use Wireshark to observe the traffic on my network, the installation was pretty easy.
Installation steps:
1. Download the sniffer firmware: nRF Sniffer for Bluetooth LE v4.1.0.
Extract the archive and find the hex file that matches your DK or Dongle.
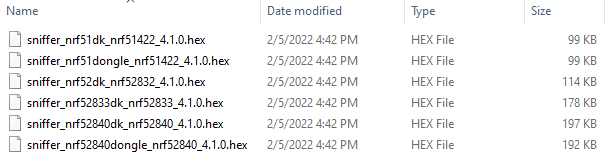
2. Program the dongle.
I have nRF Connect for Desktop already installed on my PC and it has a Programmer app, so I used that. Basically just select the device, drag & drop the hex file, and write the device.
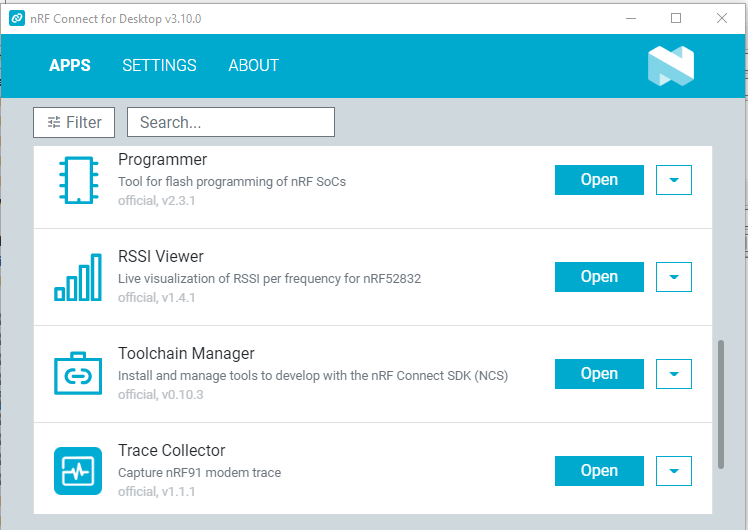
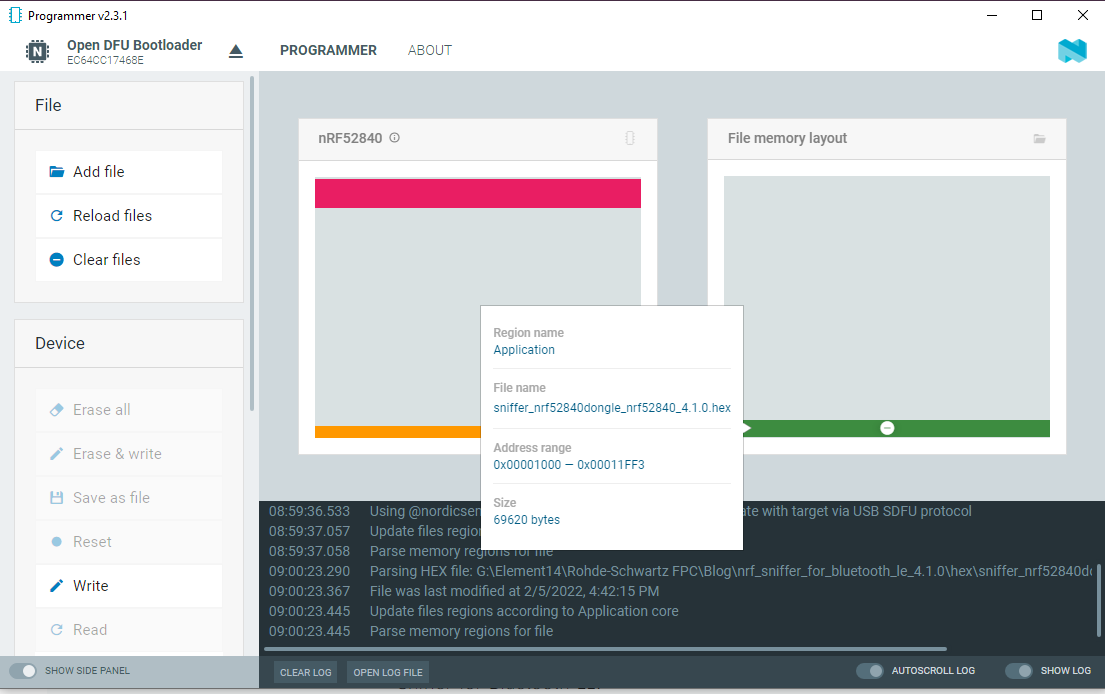
3. Install the nRF Sniffer capture tool.
The nRF Sniffer is installed as an external capture plugin in Wireshark. Wireshark is a free software tool that captures network traffic and reproduces it in a readable format. It is a cross-platform network protocol analyzer that can be used to view, analyze, and troubleshoot packets sent over a data network.
There are some software requirements that must be met:
Software requirements
- Supported operating systems:
- Windows 10
- 64-bit OS X/macOS 10.6 or later
- Linux (check the Wireshark prerequisites for version compatibility)
- Wireshark v3.4.7 or later
- Python v3.6 or later
The installation instructions are straightforward, so I won't go through them in detail. It is basically a two step process:
- Copy the nRF Sniffer capture tool into Wireshark's folder for personal external capture plugin
- Add a Wireshark configuration profile for the nRF Sniffer
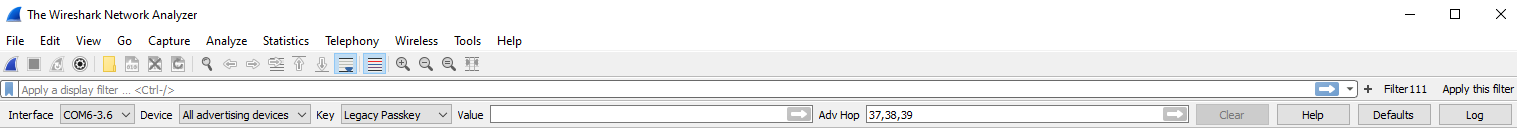
Running the nRF Sniffer:
1. Open Wireshark
2. Open nRF Sniffer Toolbar
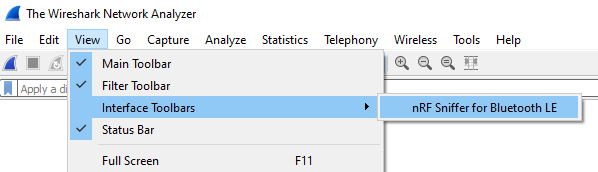
3. Select nRF Sniffer as Capture source

4. Click the Blue Shark fin in the toolbar to start capturing
5. Example of capture of advertising packets from nearby BLE devices

Next steps
Now that I've got things running, it's time to familiarize myself with the tool and learn how to isolate specific target traffic using display filters. I'm starting to realize the enormous amount of BLE traffic that I have in my house, not to mention all the WiFi traffic around 2.4GHz...
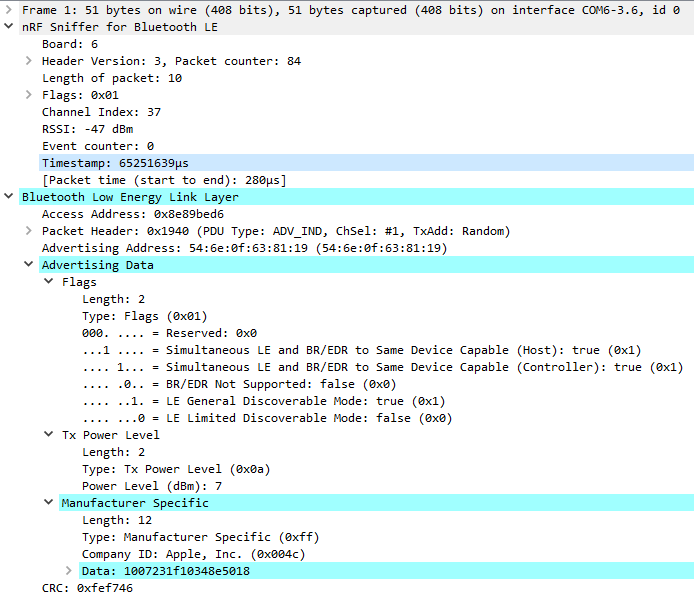
A snapshot of packet information: