1. SHA-256 (Secure Hash Algorithm)
Choice of SHA-256 as hardware acceleration would be popular since SHA-256 is keystone of Bitcoin technology.
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed "hash" (the output from execution of the algorithm) to a known and expected hash value, a person can determine the data's integrity.

Refer to SHA-256 Algorithm – Encryption – BitcoinWiki for detail.
It is idea if a one-way hash can be generated from any piece of data, but the data cannot be generated from the hash. To crack hash algorithm, many hash values were recorded in database for search. Partly, it shows the importance of HASH.
In the Hash sha256: Encryption and reverse decryption (md5hashing.net), one can get hash value and search some reserve hash value,

Try HASH "abc", got,

The core algorithm of POW(Proof of Work) is seeking one random value padded for hash value with several zero. First computer solving the math problem can packing the block and got reward of several bitcoin.
Therefore, hash algorithm is foundation of bitcoin network.
2. The program flow
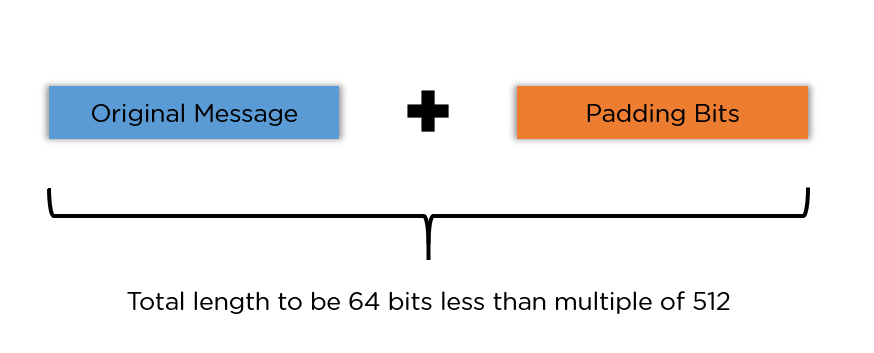
2.1 Padding
The data shall be padding with zeros after on "1" bit to integral times of 512 to start calculation,
2.2 Prepare constants
First 8 numbers of
h0 := 0x6a09e667
h1 := 0xbb67ae85
h2 := 0x3c6ef372
h3 := 0xa54ff53a
h4 := 0x510e527f
h5 := 0x9b05688c
h6 := 0x1f83d9ab
h7 := 0x5be0cd19
are initiating value, to be transfered into final 256 bit hash value. These numbers are first 32 bits of digital part of square root(2,3,5,7,11,13,17,19),
and 64 constants, labaled K[0] to K[63], similarly, first 32 bits of digital part of cube root of (2,3,5,7,11,13,17,19,23,29,31,37,41,43,47,53,59,61,67,71,73,79,83,89,97…)
428a2f98 71374491 b5c0fbcf e9b5dba5
3956c25b 59f111f1 923f82a4 ab1c5ed5
d807aa98 12835b01 243185be 550c7dc3
72be5d74 80deb1fe 9bdc06a7 c19bf174
e49b69c1 efbe4786 0fc19dc6 240ca1cc
2de92c6f 4a7484aa 5cb0a9dc 76f988da
983e5152 a831c66d b00327c8 bf597fc7
c6e00bf3 d5a79147 06ca6351 14292967
27b70a85 2e1b2138 4d2c6dfc 53380d13
650a7354 766a0abb 81c2c92e 92722c85
a2bfe8a1 a81a664b c24b8b70 c76c51a3
d192e819 d6990624 f40e3585 106aa070
19a4c116 1e376c08 2748774c 34b0bcb5
391c0cb3 4ed8aa4a 5b9cca4f 682e6ff3
748f82ee 78a5636f 84c87814 8cc70208
90befffa a4506ceb bef9a3f7 c67178f2
2.3 Define basic function
There are combination calculation with six key functions,
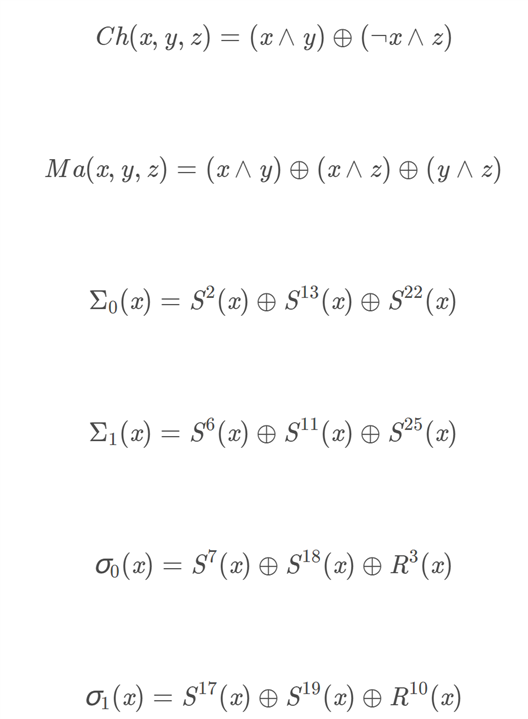
Transfer the initiate value into final hash value.
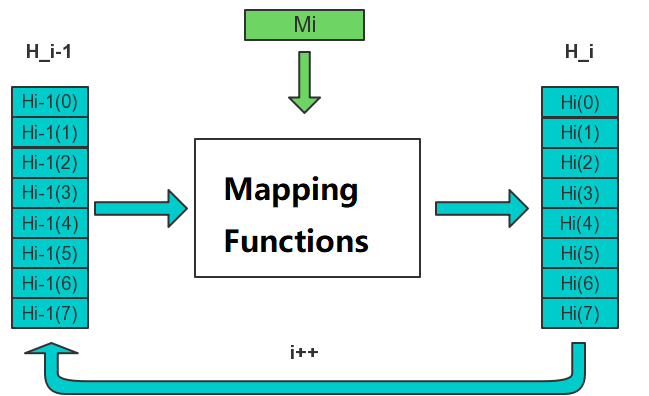
M(i) stands for raw data blocks input in series. What ever the size and value the input, final output is always 256 bits.
2.4 Program flow
Each block run 64 rounds as follows, in his graph A~H equal to H(i) in diagram above.

3. Create new project for sha256 acceleration.
Create one new project in Vivado and add verilog code for SHA256 algorithm and create new resource file in verilog for sha256
Define IN and OUT for data input and hash result output,
Create top module ,
reserve input and output blank for function test, it shall be revised to UART, I2C or AXI buffing for different kinds of data sources.
Now the codes are complet and ready to build
4.Code in verilog
The hash code in verilog as detailed in part 2,
module sha256_hash_hw(
input IN,
output OUT
);
input [0:31] IN;
output [0:255] OUT;
reg [0:31] IN;
reg [0:255] OUT;
reg [0:31] H0;
reg [0:31] H1;
reg [0:31] H2;
reg [0:31] H3;
reg [0:31] H4;
reg [0:31] H5;
reg [0:31] H6;
reg [0:31] H7;
reg [0:31] k[0:63];
reg [0:31] w[0:63];
reg [0:511] message;
integer i;
reg [0:31] s0;
reg [0:31] s1;
reg [0:31] sum0;
reg [0:31] sum1;
reg [0:31] Ma;
reg [0:31] Ch;
reg [0:31] t1;
reg [0:31] t2;
reg [0:31] a;
reg [0:31] b;
reg [0:31] c;
reg [0:31] d;
reg [0:31] e;
reg [0:31] f;
reg [0:31] g;
reg [0:31] h;
always @(IN)
begin
k[0] = 32'h428a2f98;
k[1] = 32'h71374491;
k[2] = 32'hb5c0fbcf;
k[3] = 32'he9b5dba5;
k[4] = 32'h3956c25b;
k[5] = 32'h59f111f1;
k[6] = 32'h923f82a4;
k[7] = 32'hab1c5ed5;
k[8] = 32'hd807aa98;
k[9] = 32'h12835b01;
k[10] = 32'h243185be;
k[11] = 32'h550c7dc3;
k[12] = 32'h72be5d74;
k[13] = 32'h80deb1fe;
k[14] = 32'h9bdc06a7;
k[15] = 32'hc19bf174;
k[16] = 32'he49b69c1;
k[17] = 32'hefbe4786;
k[18] = 32'h0fc19dc6;
k[19] = 32'h240ca1cc;
k[20] = 32'h2de92c6f;
k[21] = 32'h4a7484aa;
k[22] = 32'h5cb0a9dc;
k[23] = 32'h76f988da;
k[24] = 32'h983e5152;
k[25] = 32'ha831c66d;
k[26] = 32'hb00327c8;
k[27] = 32'hbf597fc7;
k[28] = 32'hc6e00bf3;
k[29] = 32'hd5a79147;
k[30] = 32'h06ca6351;
k[31] = 32'h14292967;
k[32] = 32'h27b70a85;
k[33] = 32'h2e1b2138;
k[34] = 32'h4d2c6dfc;
k[35] = 32'h53380d13;
k[36] = 32'h650a7354;
k[37] = 32'h766a0abb;
k[38] = 32'h81c2c92e;
k[39] = 32'h92722c85;
k[40] = 32'ha2bfe8a1;
k[41] = 32'ha81a664b;
k[42] = 32'hc24b8b70;
k[43] = 32'hc76c51a3;
k[44] = 32'hd192e819;
k[45] = 32'hd6990624;
k[46] = 32'hf40e3585;
k[47] = 32'h106aa070;
k[48] = 32'h19a4c116;
k[49] = 32'h1e376c08;
k[50] = 32'h2748774c;
k[51] = 32'h34b0bcb5;
k[52] = 32'h391c0cb3;
k[53] = 32'h4ed8aa4a;
k[54] = 32'h5b9cca4f;
k[55] = 32'h682e6ff3;
k[56] = 32'h748f82ee;
k[57] = 32'h78a5636f;
k[58] = 32'h84c87814;
k[59] = 32'h8cc70208;
k[60] = 32'h90befffa;
k[61] = 32'ha4506ceb;
k[62] = 32'hbef9a3f7;
k[63] = 32'hc67178f2;
H0 = 32'h6a09e667;
H1 = 32'hbb67ae85;
H2 = 32'h3c6ef372;
H3 = 32'ha54ff53a;
H4 = 32'h510e527f;
H5 = 32'h9b05688c;
H6 = 32'h1f83d9ab;
H7 = 32'h5be0cd19;
message = {IN[0:31], 1'b1, 415'b0, 64'h20};
for (i = 0; i < 16; i = i + 1)
begin
w[i] = message[0:31];
message = message << 32;
end
for (i = 16; i < 64; i = i+1)
begin
s0 = {w[i-15][25:31], w[i-15][0:24]} ^ {w[i-15][14:31], w[i-15][0:13]} ^ (w[i-15] >> 3);
s1 = {w[i-2][15:31], w[i-2][0:14]} ^ {w[i-2][13:31], w[i-2][0:12]} ^ (w[i-2] >> 10);
w[i] = w[i-16] + s0 + w[i-7] + s1;
end
a = H0;
b = H1;
c = H2;
d = H3;
e = H4;
f = H5;
g = H6;
h = H7;
for (i = 0; i < 64; i = i+1)
begin
sum0 = {a[30:31], a[0:29]} ^ {a[19:31], a[0:18]} ^ {a[10:31], a[0:9]};
Ma = (a & b) ^ (a & c) ^ (b & c);
t2 = sum0 + Ma;
sum1 = {e[26:31], e[0:25]} ^ {e[21:31], e[0:20]} ^ {e[7:31],e[0:6]};
Ch = (e & f) ^ ((~e) & g);
t1 = h + sum1 + Ch + k[i] + w[i];
h = g;
g = f;
f = e;
e = d + t1;
d = c;
c = b;
b = a;
a = t1 + t2;
end
H0 = H0 + a;
H1 = H1 + b;
H2 = H2 + c;
H3 = H3 + d;
H4 = H4 + e;
H5 = H5 + f;
H6 = H6 + g;
H7 = H7 + h;
OUT = {H0, H1, H2, H3, H4, H5, H6, H7};
end
endmodule
The top module,
`timescale 1ns / 1ps
module top_hash(
);
output [0:31] IN;
input [0:255] OUT;
reg [0:31] IN=32'h12345678;
reg [0:255] OUT;
sha256_hash_hw HASH (
.IN (IN),
.OUT (OUT)
);
5.Make the Hardware Acceleration
Build and flash the bitstream in COMD-S7 can test how the SHA256 goes.
