Internet of Things
IoT Cybersecurity best practices
Common Cybersecurity specifications
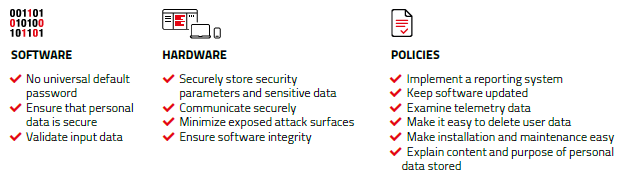
Best practices to implement in any IoT application
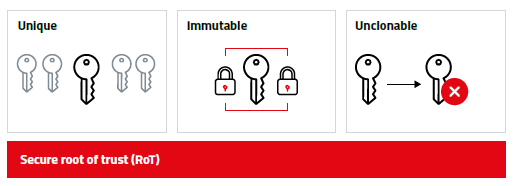
A secure root of trust is a unique identity and a cryptographic key associated with it. Since the entire chain of security relies on this root of trust, it is essential to have a RoT that is unique, immutable and unclonable.
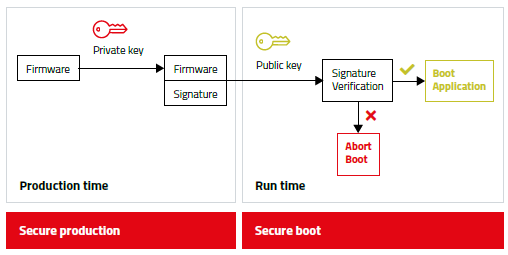
Secure boot is a security feature that ensures only trusted software is loaded during the boot process of a device. It is a firmware-based process that verifies the digital signature of the boot loader and any subsequent operating system components before they are loaded into the memory. The goal of secure boot is to prevent malware and other malicious software from executing during the boot process and compromising the system.
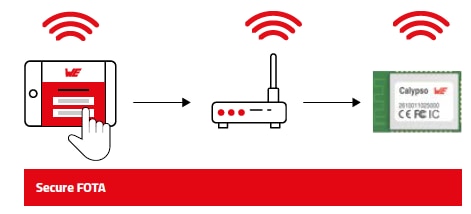
Firmware over-the-air (FOTA) is a process where the firmware of an electronic device is updated wirelessly, typically through a secure connection. FOTA updates can be used to deploy bug fixes, add new features, or patch security vulnerabilities in the device’s firmware.

Any interface to the outside world needs to be consider as vulnerable and needs to be secured. A set of standard protocols can be used to for authentication and encryption of communication interfaces.
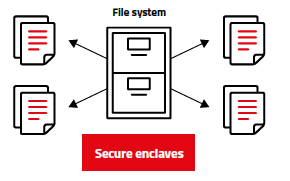
Secure enclaves are isolated execution environments that provide hardware-based security for sensitive data and code. They are designed to protect against attacks that attempt to access or modify data in memory or steal cryptographic keys.
If you want to read more find here the whole Product Guide.

