RoadTest: Infineon Trust Platform Module + Raspberry Pi 3 B
Author: skruglewicz
Creation date:
Evaluation Type: Evaluation Boards
Did you receive all parts the manufacturer stated would be included in the package?: True
What other parts do you consider comparable to this product?: First time experience with a TPM, so no comment on this question.
What were the biggest problems encountered?: Getting the Encryption/Decryption Tools and programming to work. This is not a problem with this review TPM, but with the Open source software configuration
Detailed Review:
This RoadTest review will evaluate the Infineon OPTIGA TPM SLM 8670 Iridium Add-on Board for the Raspberry PI

UPDATE TSS Programming Section 6 March 15 2022
The board is fully compliant with the Trusted Platform Module (TPM)standards issued by the Trusted Computing Group (TCG)
The module contains a female header that supports SPI which connects to the GPIO on a raspberry PI 3. The TSG spec defines the pin connections over an SPI interface.
The evaluation board contains the Infineon OPTIGA SLM 9670AQ2.0 security chip.
The module is used to evaluate compliance with the Open SourceTSS2 Stack.
An Raspberry PI 3 Model B, is supplied with the kit reviewed. The RPI needs to be configured and flashed with a Linux operating system to a supplied MicroSDHC class 10 card. An micro USB cable is also supplied in the kit.
The RPI uses the Linux operating system as a host to the Open Source TSS and Tools.
An extensive108 page guide by Infineon is used to show the integration of the open source TPM Stack 2.0 on a Raspberry Pi Linux environment with the OPTIGA TPM SLM 9670 board. The Document is called "OPTIGA TPM Application Notes" Revision 1.2 2020-8-10. This document contains step-by-step instructions on How-To setup the Open Source TPM software stack 2.0 (tss2.0) and related software on a raspberry PI 3 Linux environment to communicate with the Trusted Platform Module (TPM) OPTIGA TPM SLM 9670 TPM Iridium board.

NOTE : As of this review writing, an updated Raspberry PI OS has been release for all models of the PI's. The new version is Debian 11 (code name BULLSEYE.)..The RPI OS is based on the Linux Debian distro, which is upgrade to a major release every 2 Years.. The PI organization like to code name the OS version with TOY STORY characters... cute.
This guide was tested on a Raspberry Pi (RPI) 3 Model B with Raspberry Pi OS (32-bit) Lite, a minimal image based on Debian 10 (Buster), and kernel version 4.19 is used The full version of BUSTER OS will also work, on a bigger SD card. this is what I'm using for this review.
More on installing the OS latter.
My goals for this review are:
I will be evaluating the use and helpfulness of customer support on the OPTIGA TPM SLM 9670 TPM Iridium board. kit. I will also be discovering and evaluating the available User Forums and Knowledge Base available on the Infineon Web Site, that hopefully will aid me in my experiments. I will also be using the Resources (Documentation, Video's, Tutorials ) available on the Website. I will be including links throughout my review and in the "references" section at the end of this review.
The TPM board is contained in a box along with a Raspberry PI 3 Model B, 8GB microSDHC card, Micro USB cable and a Quick Start Guide. The box was contained in a well padded shipping box from Newark. This section describes the contents in photo and describes the " Quick Start Guide"
 |
 |
 |
 |
 |
|
 |
The OPTIGA TPM module contains a female header that supports SPI which connects to the GPIO on a raspberry PI 3 as Described here. |
 |
 |
 |
 |
| FRONT |
BACk |
 |
 |
| PAGE 1 | PAGE 2 |
NOTE : As of this review writing, an updated Raspberry PI OS has been released for all models of the PI's. These 3 links describe the setup of this OS version on the newest Raspberry PI 4 .Model B.
This version is brand new and is known not to work with the TSS.
The new version is Debian 11 (code name BULLSEYE.)..
This RPI OS is based on the Linux Debian distro, which is upgrade to a major release every 2 Years..
.Skip that Step in the OS setup.

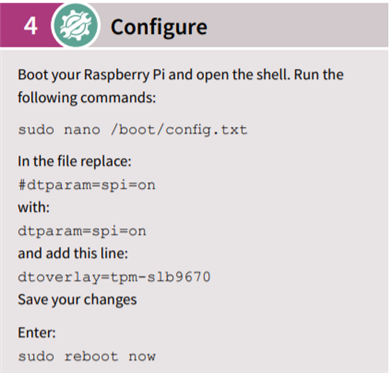
![]()

1 The TPM Software Stack (TSS)
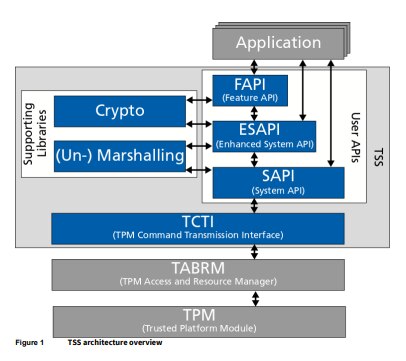
2 Setup and Usage Environment
3 Installed Software Overview
This guide focuses on installing five software components for use with the TPM. These are
1. TPM Software Stack 2.0 (tpm2-tss)
2. TPM2 Access Broker & Resource Manager (tpm2-abrmd)
3. TPM2 Tools (tpm2-tools)
4. TPM2 TSS Engine (tpm2-tss-engine)
5. Cryptsetup (cryptsetup)
6. PKCS#11 (tpm2-pkcs11)
The Chspter goes on to explain what these components are.

4 TSS Setup
5 TSS Usage
6 TSS Programming


 |
2020-02-13-raspbian-buster.zip | 2020-02-13 16:21 | 1.1G |
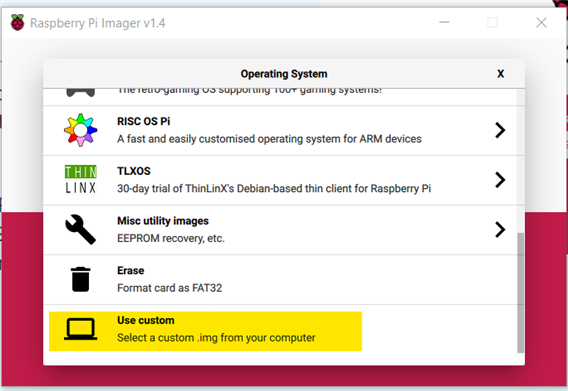
Since the Buster OS is not Available on the PI Imager this video will demonstrate how to get the image and flash it to an SD card.
The complete video is available on YouTube here